In the evolving landscape of software development, DevSecOps has emerged as a crucial framework that blends development, security, and operations into a seamless and collaborative process. As DevOps practices matured, integrating security became essential—thus DevSecOps was born.
DevSecOps Periodic Table
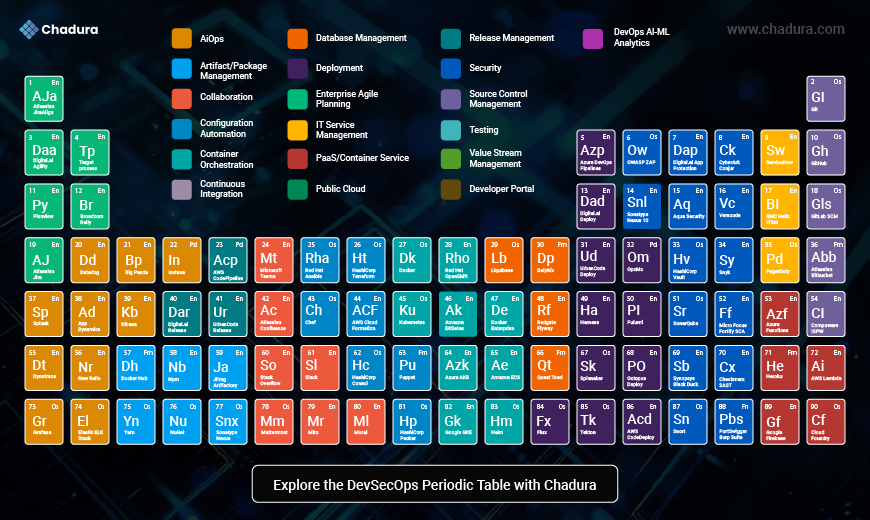
This image is a visual representation of the “DevSecOps Periodic Table”—designed by Chadura Tech—and it mimics the layout of a traditional chemical periodic table to present a categorized view of key tools and platforms used in DevSecOps (Development, Security, and Operations).It organizes the key tools, practices, and categories involved in secure DevOps (DevSecOps). Inspired by the chemical periodic table, it groups essential elements like source control, CI/CD, security, testing, cloud services, collaboration, and more into color-coded blocks. Each "element" represents a specific tool or platform used in the software delivery pipeline. It serves as a practical guide for teams to implement, evaluate, and optimize security across every stage of the DevOps lifecycle.
Explanation of the Table
Structure:
Each "element" in the table represents a tool, service, or platform used in various stages of software development, security, and operations.
Just like in chemistry, elements are color-coded and grouped based on their functionality or category within DevSecOps.
Color-Coded Categories
Each color in the table represents a specific category:
| Color | Category |
|---|---|
| 🟧 Orange | AIOps, Release Management, Security |
| 🟦 Blue | Artifact/Package Management, Collaboration, Continuous Integration, Source Control |
| 🟥 Red | Testing |
| 🟨 Yellow | Configuration, Container Orchestration |
| 🟪 Purple | DevOps AI-ML Analytics |
| 🟩 Green | Public Cloud, PaaS, Agile, etc. |
| 🟫 Brown | Developer Portals, Value Stream |
| ⚫ Black | Database, Deployment, EAP, ITSM |
Key Components in the Table
- Top Left (Green Section): Tools like AJa, Daa, Py, Tp indicate public cloud and platform services (e.g., AWS, Azure, GCP, Terraform, etc.)
- Blue Blocks: Represent tools for CI/CD, Package Management, and Collaboration (e.g., Jenkins, GitLab, Slack)
- Red Blocks: Testing tools (e.g., Selenium, Postman)
- Orange Blocks: Include Security and Release Management tools
- Purple Section (Top Right): DevOps AI/ML Analytics tools
- Center Row: Mixed categories showing critical deployment, configuration, and monitoring tools
How to Use the DevSecOps Periodic Table
Organizations can use the table as:
- A roadmap for implementing DevSecOps practices.
- A gap analysis tool to identify missing or weak areas.
- A training resource for teams to explore tools and responsibilities.
- A communication bridge across development, security, and ops teams.
It’s a dynamic reference, helping teams shift security left and build it into every step of the SDLC (Software Development Life Cycle).
Sample Toolchain Derived from the Table
Here’s a sample DevSecOps pipeline built using the periodic table:
Sample DevSecOps Pipeline (Explained)
1. Planning & Governance
- Jira – Used for project planning, issue tracking, and sprint management.
- Risk Register – Helps document, assess, and monitor project risks from the beginning.
- Purpose: Ensures compliance, visibility, and that security considerations are addressed from the planning stage.
2. Code & SAST (Static Application Security Testing)
- GitHub – Code repository and version control system; also supports security scanning.
- SonarQube – Performs SAST by scanning source code for bugs, vulnerabilities, and code smells.
- Purpose: Catch insecure code patterns before the software is built or deployed.
3. Build
- Jenkins – Automates the build process (CI/CD).
- Snyk – Scans open-source libraries and dependencies in the codebase for known vulnerabilities
- Purpose: Automate code compilation while scanning third-party packages for threats.
4. Infrastructure as Code (IaC)
- Terraform – Automates infrastructure provisioning (cloud, VMs, networks).
- Checkov – Scans Terraform scripts for misconfigurations and policy violations
- Purpose: Secure your cloud infrastructure from the ground up.
5. Containers
- Docker – Used to package applications into containers.
- Trivy – Scans container images for vulnerabilities, secrets, and license issues.
- Kubernetes Admission Controllers – Validate or reject workloads before they run in a cluster, enforcing security policies.
- Purpose: Secure the container lifecycle, including image scanning and runtime policy enforcement.
6. Secrets Management
- HashiCorp Vault – Safely stores and accesses secrets (e.g., API keys, passwords, tokens).
- Purpose: Prevent hard-coded credentials and secure sensitive data access.
7. Monitoring
- ELK Stack (Elasticsearch, Logstash, Kibana) – Centralized logging, search, and visualization.
- Prometheus – Monitors metrics, performance, and system health.
- Purpose: Detect anomalies, performance issues, or suspicious behavior in real-time.
8. Threat Intelligence
- ThreatConnect – Aggregates and correlates threat data (e.g., malware, IPs).
- OSINT (Open Source Intelligence) – Uses public data sources to track emerging threats.
- Purpose: Stay proactive by tracking external threats that could affect your application or infrastructure.
9. Incident Response
- PagerDuty – Alerting and on-call scheduling for critical incidents.
- TheHive – Security incident response platform for managing investigations and casework.
- Purpose: Fast and efficient response to security breaches or anomalies.
10. DAST/IAST (Dynamic & Interactive Security Testing)
- OWASP ZAP – Open-source DAST tool that simulates attacks against a running app.
- Contrast Security – IAST tool that integrates with the app to detect vulnerabilities from inside during runtime
- Purpose: Identify vulnerabilities in live environments or staging before release.
How You Can Use It
- As a reference guide when building or upgrading your DevSecOps pipeline
- For training and onboarding team members
- During tool evaluations or budget planning
- To communicate roles and responsibilities across departments
Uses of the DevSecOps Periodic Table
The DevSecOps Periodic Table is more than a visual aid—it's a practical, strategic tool used across teams and organizations to guide secure software development. Here are its key uses:
DevSecOps Pipeline Planning
- Helps design and map out a complete, secure DevOps pipeline.
- Visualizes which tools are needed at each stage (coding, building, testing, deploying, monitoring).
Training & Education
- Used as an educational resource for developers, DevOps engineers, and security teams.
- Helps new team members understand the full DevSecOps lifecycle.
Tool Selection & Evaluation
- Assists in comparing tools across categories (e.g., DAST vs. SAST tools).
- Useful during procurement or when replacing legacy tools.
Gap Analysis
- Helps teams identify missing elements or weaknesses in their existing toolchain.
- Promotes better alignment between security, development, and operations.
Cross-Team Communication
- Serves as a common reference point for dev, sec, and ops teams.
- Makes it easier to discuss responsibilities, priorities, and tool integrations.
DevSecOps Maturity Assessment
- Organizations can use it to assess where they stand in terms of DevSecOps readiness.
- Helps structure roadmaps for improvement and automation.
DevOps Presentations & Strategy
- Great for explaining DevSecOps strategy to leadership and stakeholders.
- Visually communicates complex processes in a simple format.
Final Conclusion from a DevOps Perspective
From a DevOps standpoint, the DevSecOps Periodic Table is an essential tool that aligns perfectly with the core DevOps principles of collaboration, automation, continuous delivery, and feedback loops—but with security integrated at every stage.
In traditional DevOps, security often came last, creating bottlenecks and reactive responses to vulnerabilities. The periodic table solves this by providing a comprehensive, visual map of tools and practices that embed security directly into the DevOps lifecycle—shifting security left without slowing down delivery.
It enables DevOps teams to:
- Visualize their end-to-end toolchain in the context of security
- Select the right tools for each phase (code, build, test, deploy, monitor)
- Foster shared responsibility between Dev, Sec, and Ops teams
- Automate security checks as part of CI/CD
- Continuously improve pipeline security with visibility and feedback