AWS_IAM POLICY
I AM
AWS Identity and Access Management (IAM) is a secure service that helps you manage access to AWS resources by creating users, groups, roles, and policies. It allows you to control who can do what in your AWS environment, with fine-grained permissions.
Policies
IAM Policies in AWS are JSON documents that define permissions for users, roles, or groups. They specify what actions are allowed or denied on which AWS resources, enabling fine-grained access control across your AWS environment.
An IAM policy is a JSON document that specifies permissions. Policies can be reused with different services in AWS. The same policy can be assigned to different people and teams. Policies are of two types in AWS:
- AWS Managed Policies: These are the policies that are provided by default in AWS. These consist of the commonly used services and the read and write permissions associated with them.
- Customer-Managed Policies: In case a user needs a policy that should meet their specific needs and use cases, then they can build their custom policies.
- Multi-Factor Authentication (MFA): For an added layer of security, IAM supports MFA, which requires users to provide a second form of authentication (like a one-time password) in addition to their regular credentials.
- Granular Control Using Policies: IAM policies are JSON-based documents that allow you to control access at a granular level. You can apply these policies to users, groups, or roles to define what actions they can take on specific AWS resources.
- Identity Federation: IAM supports identity federation, which allows users outside of AWS (like those from your organization’s Active Directory or third-party identity providers) to access AWS resources without needing a separate IAM user account
Policies and Permissions in AWS Identity and Access Management
In AWS IAM policies are the backbone of managing permissions. These policies specify what actions are allowed or denied on AWS resources, helping you enforce security and control. Policies can be attached to IAM users, groups or roles and they enable you to implement the principle of least privilege allowing users to perform only the tasks they need.
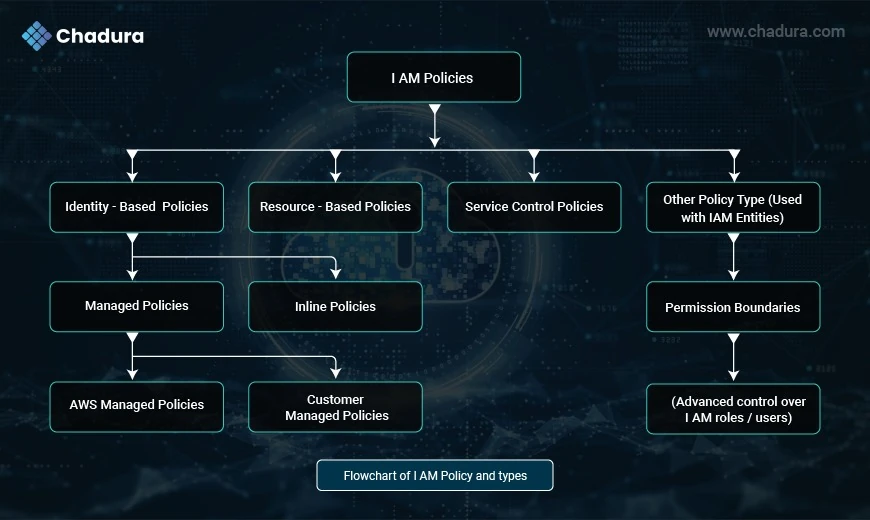
Types of IAM Policies
Managed Policies
Inline Policies
Resource-Based Policies
Permission Boundaries
Service Control Policies (SCPs)
Managed Policies
Managed Policies are reusable IAM policies that can be attached to multiple users, groups, or roles. These are maintained either by AWS or by the user (you).
There are two types:
AWS Managed Policies
Created and maintained by AWS.
Designed to provide permissions for common use cases (e.g., full access to Amazon S3).
Examples
- AmazonS3FullAccess
- AmazonEC2ReadOnlyAccess
- AdministratorAccess
- CloudWatchLogsFullAccess
Advantages
- No need to write your own JSON policy.
- Automatically updated by AWS to accommodate service changes.
Limitations
- Not customizable.
- May include broader permissions than you require (least privilege principle might be violated).
Customer Managed Policies
- Created and managed by you (the AWS user).
- Fully customizable for specific use cases.
- You define permissions in JSON and can version them.
Advantages
- Fine-grained control over access.
- Ideal for custom applications or compliance needs.
Limitations
- Requires manual updates if services change.
- You are responsible for security and correctness.
Why Use Managed Policies?
- Faster and easier than writing policies from scratch.
- AWS managed policies are tested and updated by AWS.
- Useful for standard roles (e.g., developers, auditors, S3 admins)
Policy Name | Description |
AdministratorAccess | Full access to all AWS services and resources |
AmazonEC2FullAccess | Full access to EC2 |
AmazonS3FullAccess | Full access to S3 |
AmazonRDSFullAccess | Full access to RDS |
CloudWatchFullAccess | Full access to CloudWatch |
IAMReadOnlyAccess | Read-only access to IAM |
AmazonVPCReadOnlyAccess | Read-only access to VPC |
AmazonDynamoDBFullAccess | Full access to DynamoDB |
AWSLambdaExecute | Basic permissions to run Lambda functions |
Billing | Access to AWS billing info (non-root user setup) |
Inline Policies
Inline policies are embedded directly into a single IAM user, group, or role. Unlike managed policies, which are standalone entities that can be reused, inline policies are tightly coupled with a specific identity.
When to Use Inline Policies
Use inline policies only when you want to ensure that the permissions are strictly attached to one identity and not reused elsewhere.
Ideal for:
- Roles requiring strict, isolated permissions.
- One-off permission sets not needed elsewhere.
- Audit or compliance requirements where explicit bindings are necessary.
Resource-Based Policies
- Unlike the first two types, which are attached to users, roles, or groups, resource-based policies are attached directly to AWS resources, such as S3 buckets, Lambda functions, or SNS topics. These policies define which principals (users, roles, or services) are allowed to access the resource and what actions they can perform. Resource-based policies are useful for controlling cross-account access to resources.
Permission Boundaries
- These are advanced policies that set limits on the maximum permissions an IAM user or role can receive. Permission boundaries do not grant any additional permissions but act as a restriction, ensuring that policies attached to a user or role do not exceed the boundaries. This is particularly useful for delegating permissions to others while maintaining control over security.
Service Control Policies (SCPs)
- SCPs are used in AWS Organizations to manage permissions for all accounts within an organization or organizational unit (OU). They define the maximum level of permissions that can be assigned to any user, role, or group within the accounts governed by the organization. SCPs help ensure compliance and governance across multiple AWS accounts.
Permissions in AWS IAM Policies
Permissions within an IAM policy define what actions are allowed or denied for specific AWS resources. The policy includes the following elements:
- Actions: Specifies the API operations (like s3:PutObject or ec2:StartInstances) that the policy allows or denies.
- Resources: Defines the specific AWS resources the policy applies to (like an S3 bucket or EC2 instance).
- Effect: Determines whether the action is allowed (Allow) or denied (Deny).
- Conditions: Optional, but they add an additional layer of control by specifying conditions under which the policy is in effect (for example, restricting actions based on the requester's IP address or the time of day).
IAM Policy Document Structure
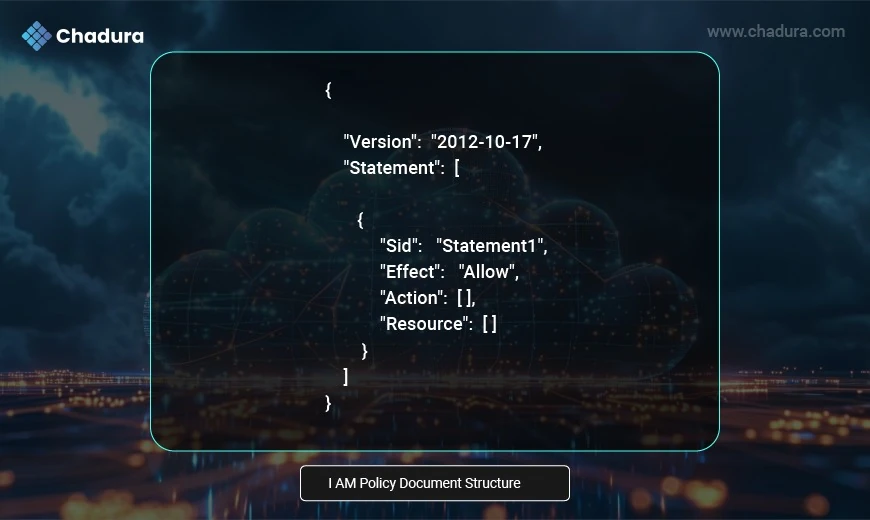
To fully understand the structure of an IAM policy, let us see the default template provided by AWS and look at all the fields one by one.
- Version-ID: This is a compulsory field in a policy that is uniquely used to identify a JSON policy.
- Statement: It defines the permission for a single resource.
- Sid: Is short for statement id. It is a unique identifier for a statement.
- Effect: It defines the Allow/Deny prospects to a resource.
- Action: This is used to state what service can perform what all actions.
- Resource: It consists of the list of resources that are impacted by the policy.
Final Conclusion
IAM policies are the cornerstone of security in AWS. From simple managed permissions to fine-grained inline rules and cross-account sharing via resource-based policies, they offer the flexibility and control required to run secure cloud workloads.