SSH
The Secure Shell (SSH) network protocol uses encryption to allow two connected devices—usually a server and a client—to communicate securely with one another. It enables users to safely command and control distant machines. Conventional methods that transfer data in plain text, such as Telnet, FTP, and login, can be safely replaced with SSH. File transfers, network service tunneling, and remote administration are among its common uses.
What does SSH do?
Secure Communication: Client and server can communicate securely because of SSH. It encrypts all the data that is being communicated over the network so that the data cannot be accessed by unauthorized users, including passwords, usernames, and other sensitive data.
Authentication: SSH provides methods of authenticating the server and client to ensure their legitimacy. To establish the identities of the parties, it employs cryptographic keys. Only legitimate servers and users can access the system due to this authentication.
Encryption of Data Transfer: SSH encrypts all data that is in transit between client and server so that it cannot be intercepted and read or modified by unauthorized users. Data integrity and confidentiality during transfer are ensured by this encryption.
Remote Access: SSH is mostly employed to provide secure remote access to computers, servers, and other resources. SSH allows users to securely execute remote commands or remotely access a server's command-line interface.
File Transfer: SSH facilitates secure file transfer from one computer to another through tools such as Secure Copy Program (SCP) and SSH File Transfer Protocol (SFTP). SSH can be used to transfer data securely from one remote server to another remote server or from a local machine to a remote server.
Tunneling: It is facilitated by the tunneling feature of SSH to create secure channels for the passing of other network protocols over SSH. Services that are not available on the network directly otherwise, such as web servers, databases, and email servers, can now be accessed securely because of this feature.
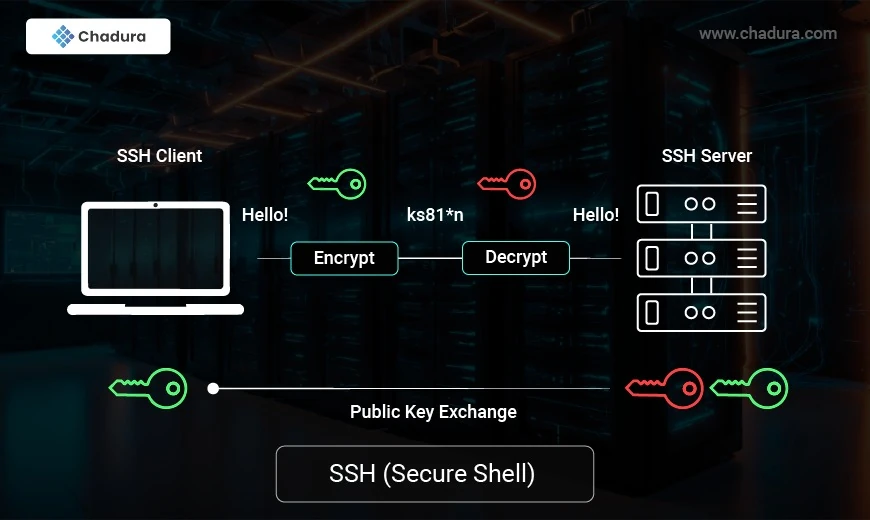
The architecture of Secure Shell
Secure Shell architecture is client-server. A server administrator would typically install a program on the server that decides to accept or decline incoming connections. There is also a client program, which a user runs on his/her PC, that makes requests to the server. The server listens on HTTP port 22 by default.
SSH used for?
Technically, SSH can transport any arbitrary data through a network, and SSH tunneling can be set up to do an unbelievably large amount of things. The most common SSH applications are, however:
1.Remote server, infrastructure, and employee computer management
2.Secure file transfer (SSH is more secure than unencrypted alternatives like FTP)
3. Usage of cloud services without exposing the ports of a local machine to the Internet
4.Remote access to the facilities of a private network
Bypassing firewall restrictions
The architecture of Secure Shell
The architecture of Secure Shell is client-server. A server administrator typically installs a program on the server that controls whether incoming connections are accepted or rejected. In addition, a client program that a user runs on their PC makes requests to the server. The server listens on HTTP port 22 by default.
Common Use Cases for SSH
Remote Server Management:
- Securely access and manage Linux/Unix servers remotely.
Secure File Transfers:
- Transfer files securely using SCP or SFTP.
Tunneling:
- Create secure tunnels for accessing restricted services (e.g., databases, web apps).
Automation:
- Use SSH in scripts for automated tasks like backups, deployments, or system monitoring.
DevOps and Cloud Operations:
- Manage cloud infrastructure, containers, and virtual machines securely.
An SSH key pair consists of two components:
- Private Key: This key is kept secure on the client’s machine and should never be shared. It is used to authenticate the user when connecting to a remote server.
- Public Key: This key can be shared and is added to the ~/.ssh/authorized_keys file on a remote server. When a user attempts to connect, the server verifies the connection using the corresponding private key.
Aspect | Private Key | Public Key |
|---|---|---|
| Purpose | Used for authentication and proving identity. | Stored on remote servers to verify the private key. |
| Storage Location | Kept securely on the client machine (~/.ssh/id_rsa). | Added to the server’s ~/.ssh/authorized_keys file. |
| Confidentiality | Must remain private and never be shared. | Can be shared with anyone or any server. |
| Security Risk | If compromised, an attacker can access all servers linked to it. | Safe to share; cannot be used alone to access a system. |
| Usage | Used when logging into a remote server. | Used by the server to verify authentication. |
What port does SSH use?
The default SSH port is 22. Firewalls tend to block access to some ports of servers that they are protecting but do not close access to port 22. Because packets traveling to port 22 are not blocked and might be forwarded to any other port, SSH proves useful when gaining access to servers that are shielded behind the firewall.
Getting Started with SSH
1. Connecting to a Remote Server
To connect to a remote server using SSH, use the following command:
ssh username@remote_hostExample: ssh user@192.168.1.12. Generating SSH Keys
Generate a public-private key pair for authentication:
ssh-keygen -t rsa -b 40963. Copying SSH Public Key to Server
Add your public key to the server’s ~/.ssh/authorized_keys file:
ssh-copy-id username@remote_host4. Using SCP for File Transfers
Copy files securely using SCP:
scp file.txt username@remote_host:/path/to/destination5. Using SFTP for Interactive File Transfers
Open an interactive SFTP session:
sftp username@remote_hostSSH Configuration File
The SSH client configuration file (~/.ssh/config) allows you to simplify and customize SSH connections. Here’s an example configuration:
Host myserver
HostName 192.168.1.1
User user
Port 2222
IdentityFile ~/.ssh/id_rsaConclusion
SSH is an indispensable tool for IT professionals, developers, and system administrators. Its ability to provide secure, encrypted communication over unsecured networks makes it a cornerstone of modern IT infrastructure. Whether you're managing remote servers, transferring files, or automating tasks, SSH ensures that your data remains secure and your operations run smoothly.