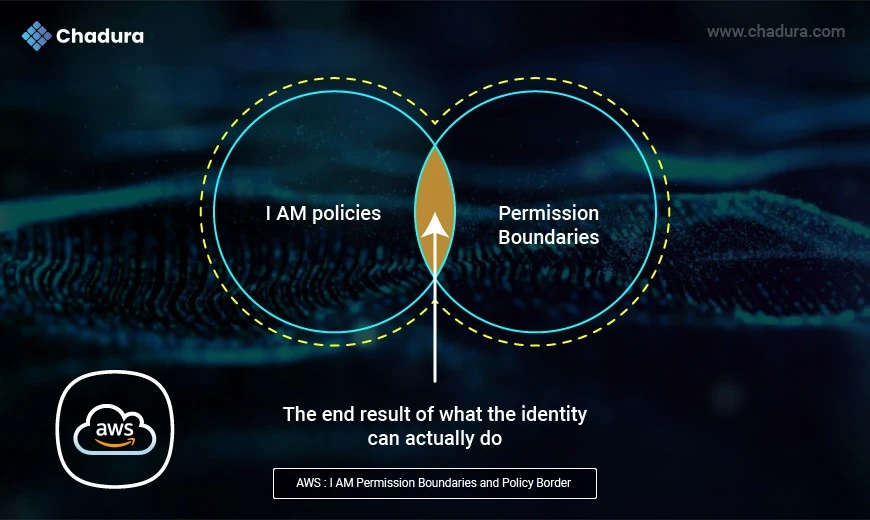
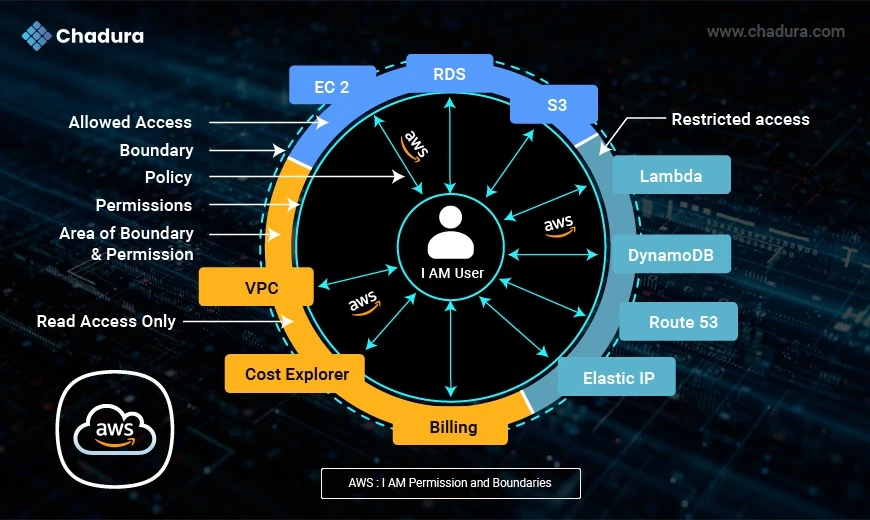
What Are AWS Permission Boundaries?
AWS Permission Boundaries serve as a crucial component of Identity and Access Management (IAM) within AWS. These boundaries act as a tool to set the maximum permissions an identity can have, ultimately ensuring that users have the appropriate level of access while maintaining security safeguards. To put it simply, AWS permission boundaries define the maximum permissions a user or role can have, effectively acting as protection against over privileged access.
AWS Permission Boundaries Work
Understanding the mechanics of an AWS permission boundary is essential for effectively implementing them. These boundaries operate by providing an additional layer of control in the AWS IAM system. When policies are attached to an IAM entity, these policies define what actions and resources a user or role can access. However, AWS permission boundaries come into play after the policies are evaluated.
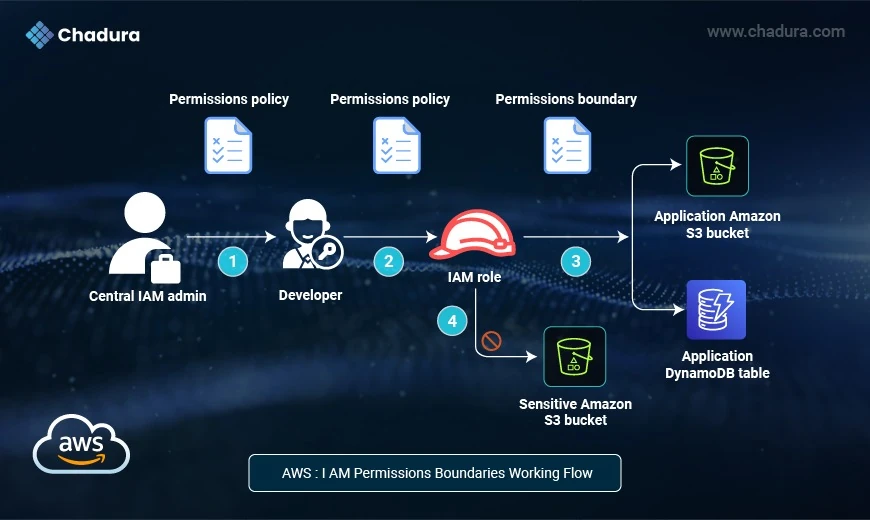
Step 1
1. Central IAM Admin Grants Developer Permissions
Component: Central IAM Admin → Developer
Action: A central IAM administrator creates a permissions policy and assigns it to the developer's IAM user.
Purpose: This policy defines what actions the developer is allowed to perform in AWS (like assuming a role).
Key Concept:
The developer cannot perform tasks directly, but can assume roles defined with specific permissions.
Step 2
2. Developer Assumes an IAM Role
Component: Developer → IAM Role
Action: The developer uses their assigned permissions to assume an IAM role that has its own set of permissions and a permissions boundary.
Purpose: This role acts as a controlled environment in which the developer can perform tasks on AWS resources.
Key Concept:
IAM roles can be constrained using permissions boundaries, which serve as the maximum allowed permissions, regardless of the role policy.
Step 3
Role Grants Access to Application Resources
Component: IAM Role → Application Amazon S3 bucket & Application DynamoDB table
Action: The permissions in the IAM role allow access to non-sensitive application resources like:
- An Amazon S3 bucket
- A DynamoDB table
Key Concept:
Even if the role policy allows more access, the permissions boundary ensures access only to approved resources.
Step 4
Role Denied Access to Sensitive Resources
Component: IAM Role → Sensitive S3 bucket (Blocked)
Action: The permissions boundary blocks access to a sensitive S3 bucket even if the role's policy allows it.
Purpose: This ensures developers cannot access high-security resources.
Key Concept:
Permissions boundaries are like a guardrail—they limit what a user or role can do, no matter what the attached permissions policy says.
Use Case Summary
A centralized IAM admin allows a developer to assume a specific role. The role has permissions to work with application-level S3 buckets and DynamoDB, but a permissions boundary ensures the developer cannot access highly sensitive resources like a protected S3 bucket.
Key Benefits of Using AWS Permission Boundaries
Now that we understand the basics, let’s explore the five key benefits of using AWS permission boundaries for access control:
1. Granular Access Control
AWS permission boundaries allow for precise control over permissions, ensuring that users or roles are granted only the permissions necessary for their specific tasks. This granular control reduces the risk of unauthorized access to critical resources.
2. Prevention of Over Privileged Users
By setting strict upper limits on permissions, AWS permission boundaries help prevent overprivileged users or roles, reducing the chances of accidental data exposure or security breaches.
3. Improved Compliance and Governance
AWS permission boundaries are a valuable tool for maintaining compliance with industry regulations and internal governance policies. They provide clear boundaries that align with compliance requirements.
4. Simplified Access & Policy Management
Managing permissions and policies becomes more straightforward with AWS permission boundaries. Instead of complex policies, you can rely on well-defined boundaries, making it easier to understand and audit permissions.
5. Scalable Permissions
As your AWS environment grows, IAM boundaries help scale with it. You can consistently enforce access control, whether you have a handful of users or a large, complex organization.
Setting Up AWS Permission Boundaries: 8 Best Practices
Implementing AWS permission boundaries effectively requires careful planning and adherence to best practices. Here are eight essential guidelines to consider:
1. Apply Permissions Boundaries to IAM Roles, Not Developers
Attach AWS permission boundaries to IAM roles rather than individual developers. This ensures consistent control over permissions across teams and simplifies management.
2. Use IAM Identity Policies and AWS Organizations SCPs
Complement AWS permission boundaries with IAM identity policies and AWS Organizations Service Control Policies (SCPs) to create a robust access control strategy.
3. Avoid Replicating Developer Policy Space to Permissions Boundaries
Setting a permission boundary should not replicate the policies developers already have. Instead, they should restrict access beyond what those policies grant.
4. Group Permissions Boundaries into Categories
Organize maximum permissions into categories based on teams or functions, making it easier to manage and track access control.
5. Adapt Boundaries to Common Business Purposes
Customize permission boundaries according to your organization’s specific needs and business processes to optimize security and efficiency.
6. Apply the Least Privilege Principle
Always adhere to the principle of least privilege, granting the minimum permissions necessary for users or roles to perform their tasks.
7. Be Conscious of Cross-Account Access
Consider the implications of cross-account access when defining AWS permission boundaries. Be vigilant in managing permissions across accounts.
8. Document and Label Accordingly
Thoroughly document your AWS permission boundaries and use clear labels to ensure proper understanding and easy maintenance.
Benefits (Pros) of Using Permissions Boundaries
- Strong Access Control:
Prevent over-permissioning even when role policies are misconfigured.
- Granular Delegation:
Admins can delegate permission management to team leads without risk.
- Compliance & Governance:
Helps enforce regulatory controls over sensitive data or actions.
- Safe Automation:
DevOps tools can be constrained to safe boundaries during CI/CD.
Security Guardrails
Permissions boundaries act as safety nets, preventing privilege escalation.
Challenges (Cons) to Consider
- Complexity in Design:
Managing layered policies (user → role → boundary) can get confusing.
- Hard to Debug:
It may be unclear why access is denied due to overlapping policy rules.
- Limited Visibility in Console:
AWS IAM console doesn’t always provide clear reasoning for access denials.
- Requires Policy Expertise:
Admins must deeply understand IAM JSON syntax and policy evaluation logic.
Best Practices
- Use boundaries with developers and automation tools.
- Log and monitor permissions with AWS CloudTrail and Access Analyzer.
- Name and document all permissions boundaries clearly.
- Test policies using AWS IAM Policy Simulator.
- Review all roles periodically for over-permissioning.
Conclusion
AWS IAM permissions boundaries are essential for scalable, secure, enterprise-grade access control. By combining them with IAM roles and permissions policies, you can create defense-in-depth access models that empower developers while protecting your most critical resources.