What is EC2 Instance Connect Endpoint (EIC)?
EIC is an AWS feature that allows you to connect to EC2 instances that are deployed in private subnets (without public IP addresses) using SSH or AWS CLI tools. It uses a VPC endpoint to enable secure, direct connectivity.
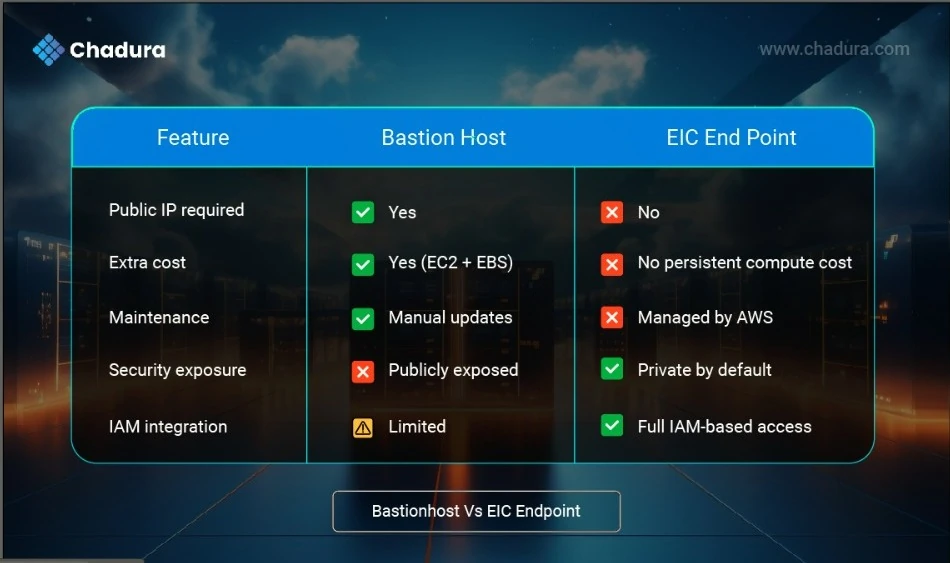
Why Use EIC Instead of a Bastion Host?
How EC2 Instance Connect Endpoint Works
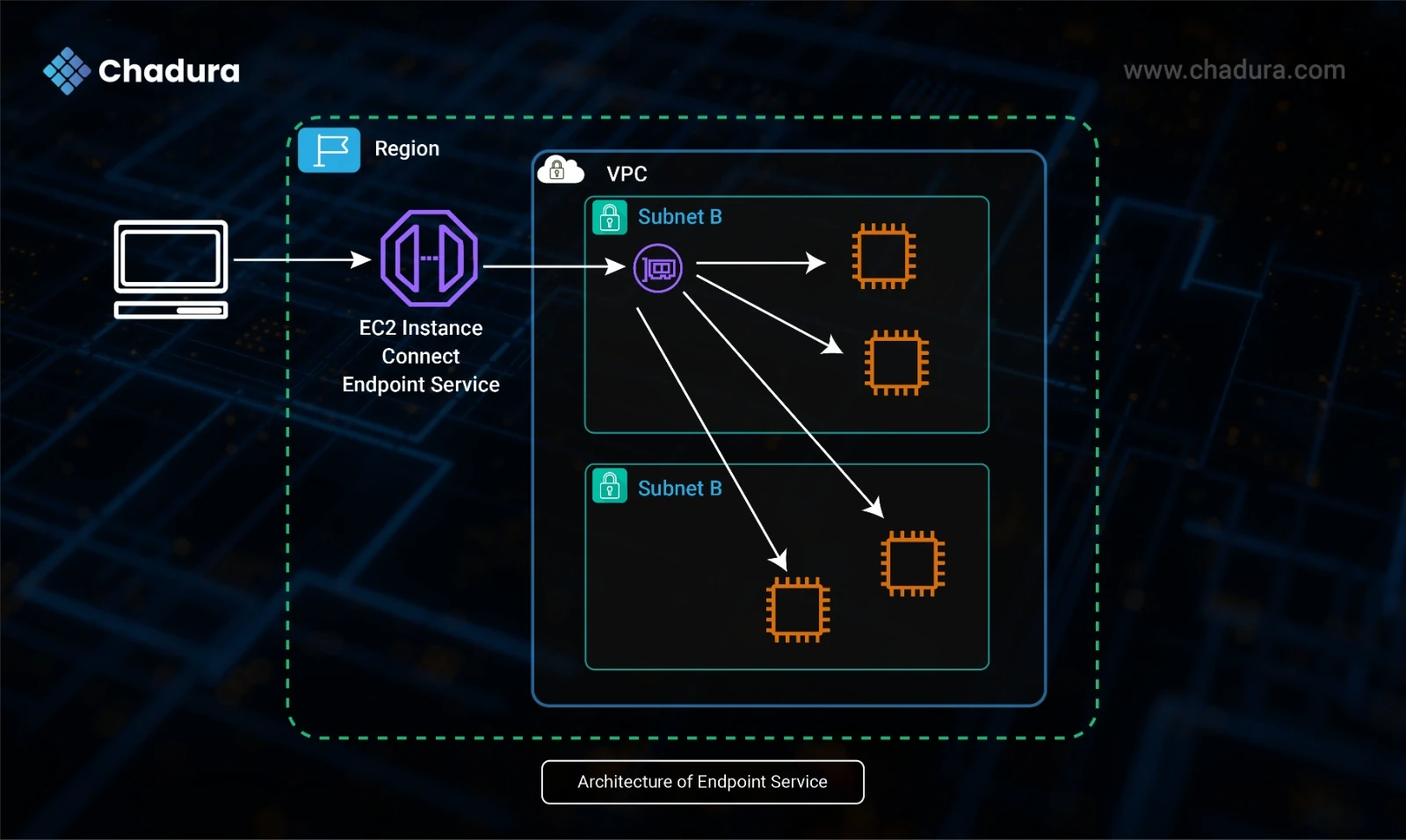
Amazon EC2 Instance Connect Endpoint is a feature that enables secure and private SSH access to EC2 instances located in private subnets, without requiring public IP addresses, bastion hosts, or VPN connections. It provides a seamless way to establish SSH connections entirely within the AWS network, using a managed network interface called an endpoint that resides in your VPC.
When a user initiates a connection via the AWS Console or CLI using EC2 Instance Connect, AWS first authenticates the user through IAM permissions. Then, a temporary SSH public key is generated and pushed to the target EC2 instance. This key is valid for a short time—typically 60 seconds—ensuring time-bound and secure access. The connection request is then routed through the EC2 Instance Connect Endpoint, which securely tunnels the traffic to the private instance within the VPC.
This method eliminates the need for maintaining and securing jump servers, managing long-lived SSH keys, or exposing instances to the internet. It leverages IAM for access control, enabling fine-grained permissions and auditability. By keeping all traffic within the AWS infrastructure, EC2 Instance Connect Endpoint enhances security while simplifying the architecture for managing EC2 instance access in private networks.
Benefits at a Glance
- Simplifies infrastructure by removing the need for jump servers.
- Enhances security by eliminating public access points.
- Enables controlled, auditable access using IAM and CloudTrail.
- Easy to set up and manage compared to traditional solutions.
Why Not Use Traditional SSH?
Traditional SSH has been the preferred way to connect to EC2 instances. It has a number of drawbacks, though:
Key Management Overhead: Dealing with, rotating, and distributing SSH keys can become complicated very fast, particularly at scale. It's a human error-prone process, creating potential security risks.
Security Risks: Lost or compromised SSH keys are a major security risk, providing unauthorized access to sensitive systems.
Increased Attack Surface: By opening SSH through port 22 and utilizing public IPs, EC2 instances are more vulnerable to attacks. With the growing rate of security incidents, leaving the ports open raises the attack surface unnecessarily.
Audit and Compliance Challenges: Tracking who accessed the instances and when, with conventional SSH, can be a complex and error-prone process. This absence of visibility is challenging for audit and compliance requirements.
Why Use AWS EC2 Instance Connect Endpoint?
The EC2 Instance Connect Endpoint solves the issues of classical SSH with multiple advantages:
Simplified Access Management: EC2 Instance Connect Endpoint employs temporary SSH keys created on a session-by-session basis, getting rid of permanent SSH key storing and management.
Improved Security:
No public IPs: Instances are kept in private subnets, minimizing internet exposure.
No exposed port 22: The EC2 Instance Connect Endpoint employs a secure, identity-aware proxy with reduced attack surfaces.
IAM Support for Fine-Grained Access Control: The access to instances is controlled with AWS IAM policies. With the integration, you can specify access based on role, allowing better control of access at a granular level.
Centralized Access Management: Administrators can manage and audit access via AWS CloudTrail, which gives visibility into exactly who accessed what instances and when.
Conclusion
EC2 Instance Connect Endpoint offers a streamlined, secure method for accessing EC2 instances in private subnets. By leveraging AWS-native tools, IAM policies, and temporary key injection, it significantly reduces the complexity and risk associated with managing SSH access in cloud environments. It's an ideal solution for organizations prioritizing security, simplicity, and scalability.