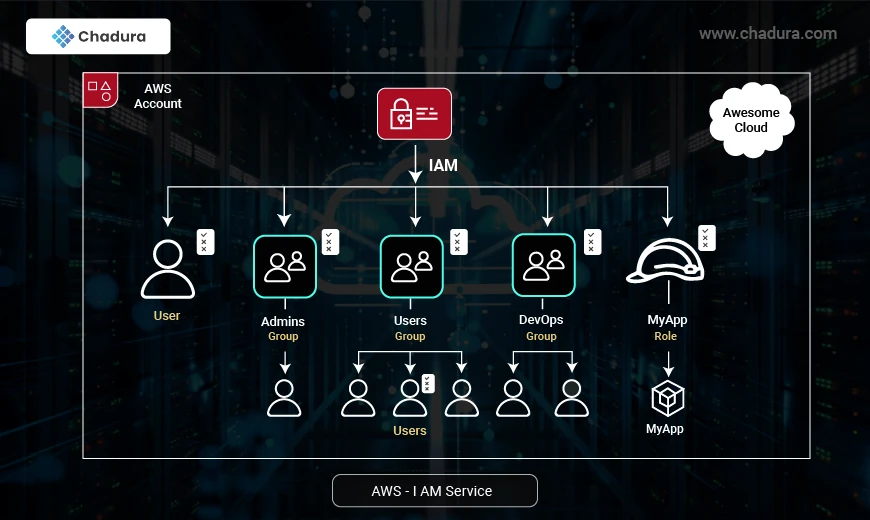
AWS Identity and Access Management (IAM) is a critical service that helps manage access to AWS resources securely. IAM allows organizations to define who can access specific resources and under what conditions. This article covers IAM Users, Roles, User Groups, and Policies in detail.
Root User
A root user is the top-level user in your AWS account in effect the 'super admin' user. Root users possess unrestricted, full permissions to use AWS resources, change permissions on users and roles, and any other action in the environment.
You should never make use of your root user for any routine tasks, even administrative tasks. You should only make use of it for the most critical tasks that can only be executed with root privileges (e.g., modifying account settings, restoring IAM user permissions, etc.).
You should ideally create your initial IAM user, then securely encrypt and store away the credentials of your root user.
What are Users in IAM?
Users are the simplest IAM identity, and define an entity that can access resources in your AWS world. A user may also be an application entity that can access those resources; for instance, a micro service that retrieves a customer's account record from your database.
By default, the user does not have any permission to do anything. While you create your initial user, you can assign it some administrative rights so that the user can create and manage IAM users, groups, and roles.
Types of IAM Users:
Human Users – Employees, administrators, or developers who require access to AWS resources.
Application Users – Software or services that use IAM credentials to interact with AWS APIs.
What are Groups in IAM?
User Groups in IAM make it easy to grant permissions to users. Rather than manually granting permissions to each user, you can form a group and grant permissions to that. Then you can assign users to the group, which automatically grants them the permissions on the group.
For instance, to give a user 'user1' admin privilege, you simply place user1 in an 'Admins' group containing the appropriate set of permissions. If user1’'s job function changes later on, you can merely remove him from the group, and he'll no longer have the particular permissions added by the Admins group.
What is an AWS IAM Role?
IAM roles are identities that you can create with certain permissions for temporary periods of time. You can delegate IAM roles to entities you trust so that those entities will be able to take on the role when necessary. IAM Roles are designed for internal use mostly.
An IAM role has no credentials (password or access keys) attached to it. One of the key differences between a User and a Role is that a role does not have credentials. A role can be temporarily taken up by a user, service, or application that has been allowed to assume the role.
What is an AWS IAM Policy?
IAM is a system of policies and technologies to secure that the proper users have proper access to technology resources. An AWS IAM policy determines the permission of an identity (users, groups, and roles) or resource in the AWS account. An AWS IAM policy controls access to AWS resources to ensure that only approved users can access given digital assets. Permissions within a policy either grant or deny the user permission to do something on a particular resource.
IAM policies may be either identity-based or resource-based.
Identity-based
Identity-based policies are linked to an identity (user, group, or role) and specify the permissions of the given identity.
Resource-based
resource-based policy specifies the permissions surrounding the particular resource—by listing which identities have access to a particular resource and when.
Implementing Conditional Access in AWS IAM Policies
Services: The first "level" of the general policy statement, AWS IAM either identifies or does not identify a particular service, such as Amazon EC2 or Amazon S3. If it doesn't identify the service, it will be marked as "uncategorized." If it identifies it, IAM will either "Allow" or "Deny" the service depending on the effect of the policy.
Actions: The IAM may identify actions or not. If identified, the action is categorized under "List," "Read," "Write," or "Permissions Management" access levels. These categories of access levels indicate how much access the action provides a user based on policy permissions.
Resources: Provides a specific key, condition, or value that indicates whether the action is compatible with a resource-level permission. One must understand that actions and resources need to be compatible. If an action does not have a compatible resource as per the IAM, then any attempt to use the action on the selected resource will be unsuccessful.
Conditions: Condition elements use condition operators (>, <, ==, etc.) to define additional constraints on actions in resources when a policy is enforced.
Condition elements are not required in the main policy statement but can specify rules that limit access to just that which is required for a user to do a particular task. This enhances security for the AWS resources being utilized in the organization.
User:
An AWS IAM Normal User is a standard IAM user created within an AWS account to access AWS resources based on assigned permissions. Unlike the root user, a normal user does not have unrestricted access to all AWS services but operates within defined security policies.
Key Characteristics of a Normal IAM User:
- Has a unique username within the AWS account.
- Requires specific permissions assigned through IAM policies.
- Can log in to the AWS Management Console with a password or access AWS services via CLI/API using access keys.
- Can be part of IAM Groups to inherit permissions collectively.
- Supports Multi-Factor Authentication (MFA) for increased security.
- Cannot modify root-level settings unless explicitly granted permissions.
Root AccessManagement
AWS Root User - Access Management Description
The AWS Root User is the initial user created when setting up an AWS account. It has full administrative access to all AWS services and resources without any restrictions. This account is linked directly to the AWS account owner's email and should be used with extreme caution.
Key Characteristics of the AWS Root User:
- Has unrestricted access to all AWS resources and services.
- Can create, modify, and delete IAM users, roles, and policies.
- Can manage billing and account settings (some of which are inaccessible to IAM users).
- Cannot be restricted by IAM policies.
- Uses the email and password associated with the AWS account for authentication.
Account Settings
AWS Account Settings - Description
AWS Account Settings refer to the configuration options available to manage and customize an AWS account. These settings control various aspects of account security, billing, access management, and resource limits.
Key Components of AWS Account Settings:
Account Details
- Includes the account name, account ID, and root user email.
- Allows updating contact information and preferences.
Billing & Cost Management
- Configure payment methods, view invoices, and manage spending limits.
- Enable AWS Budgets and Cost Allocation Tags for tracking usage.
Security Credentials
- Manage root user Multi-Factor Authentication (MFA).
- Rotate and manage access keys for IAM users.
- Enable AWS IAM Identity Center (SSO) for centralized user access.
Service Limits & Quotas
- View and request increases for AWS service limits.
- Helps optimize resource allocation for scalable applications.
Regions & Data Residency
- Select preferred AWS Regions for deploying resources.
- Control where data is stored for compliance and latency requirements.
Trusted Advisor & Support Plans
- Access AWS Trusted Advisor for best practice recommendations.
- Upgrade to AWS Support Plans for premium assistance.
Consolidated Billing (For AWS Organizations)
- Link multiple AWS accounts under one billing system for cost efficiency.
AWS Account Settings provide centralized control over account security, billing, and operational configurations, ensuring efficient and secure cloud management.
AWS Access Reports - Description
AWS Access Reports provide detailed visibility into user and service access patterns within an AWS account. These reports help administrators monitor and audit permissions, detect unusual access behavior, and ensure compliance with security policies.
Types of AWS Access Reports:
IAM Access Analyzer
- Identifies unused permissions and verifies least privilege access.
- Detects external access to AWS resources.
IAM Credential Report
- Lists all IAM users and their credentials (passwords, access keys, MFA).
- Helps track security compliance, such as password age and unused credentials.
IAM Access Advisor
- Shows the last-used timestamp for permissions granted to IAM users, roles, and groups.
- Helps identify unnecessary permissions for security optimization.
AWS CloudTrail Logs
- Tracks API calls made within an AWS account.
- Useful for forensic analysis and auditing security events.
AWS Organizations Access Reports
- Monitors access patterns across multiple linked AWS accounts.
Benefits of AWS Access Reports:
- Improve security by identifying over-provisioned permissions.
- Monitor unused or outdated IAM credentials.
- Ensure compliance with security policies and regulations.
- Detect unauthorized or suspicious access activity.
Regularly reviewing AWS Access Reports helps maintain a secure and well-governed AWS environment.
AWS IAM Security:
- Follow the principle of least privilege
- Enable Identity Federation where possible
- Rotate your access keys regularly
- Remove unused roles, users, policies, etc.