In Amazon Web Services (AWS), a bastion host is a jump server or secure gateway to give secure access to private instances (such as those in a Virtual Private Cloud — VPC) from outside the VPC. It's an ordinary security practice employed to manage and regulate access to instances in a private subnet.
Security is a priority in contemporary cloud infrastructure. A Bastion Host is a safe gateway through which administrators can connect to confidential EC2 instances within a Virtual Private Cloud (VPC) without exposing them to the internet directly. This article discusses the idea, structure, and best practices of employing a Bastion Host in AWS.
Default VPC Configuration
In a default VPC in AWS, the number of instances you can create depends on the region and the EC2 instance limits. By default, AWS provides:
- 5 VPCs per region (but you can create additional VPCs by requesting a limit increase).
- 20 EC2 instances per region (this can be increased by requesting a limit raise through the AWS support center).
- Private IP addresses: Each subnet in a VPC has a range of IP addresses, and you are limited by the available addresses in the subnet.
If you're looking at the default VPC's size, it typically uses a /16 CIDR block, which provides 65,536 private IP addresses. Subnets created within this VPC will be limited by the range of addresses assigned to them.
For instance, if you have a /24 subnet (which is common), you get 256 IP addresses (allowing up to 251 instances if you reserve some for network infrastructure).
So, the practical number of EC2 instances you can create depends on:
- The number of available IP addresses in your subnets.
- The EC2 instance limit for your AWS account (default is 20 per region).
A Bastion Host is a special-purpose server designed to withstand attacks and provide secure access to private instances in a cloud environment. It is placed in a Public Subnet and acts as an intermediary between administrators and private EC2 instances inside a Private Subnet.
Benefits of a bastion host
Secure Access Point: It acts as an entry point into your VPC from an external network (such as the internet) and provides a secure way for authorized users to access instances within private subnets.
Controlled Access: Access to instances within the private subnet is restricted, and users must first connect to the bastion host before accessing other resources in the VPC.
Hardened Security: Bastion hosts are configured with strong security measures, including strict access controls, minimal services running, regular patching, and robust authentication mechanisms (like SSH keys) to reduce vulnerabilities.
Logging and Monitoring: AWS bastion hosts can be configured to log access attempts, user activities, and network traffic. AWS CloudTrail and CloudWatch logs can be used to monitor and audit activities for security and compliance purposes.
Minimal Attack Surface: By using a bastion host, you reduce the attack surface of your private instances by allowing access only through a single, heavily secured entry point.
Dynamic Port Forwarding: Users can leverage the bastion host for dynamic port forwarding, enabling them to access other instances within the VPC via SSH tunneling.
Connect a EC2 private instance via bastion host
Launch two instances. one within a public subnet and the other within a private subnet. After that to connect a private subnet instance from public subnet instance showing below
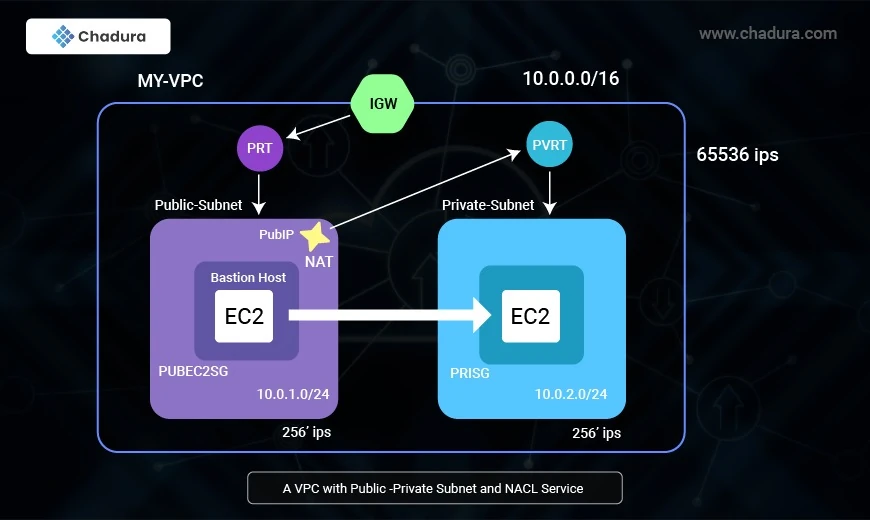
AWS Bastion Host Architecture
1. VPC and Subnets
A VPC (Virtual Private Cloud) is created with the following structure:
- Public Subnet (10.0.1.0/24): Contains the Bastion Host.
- Private Subnet (10.0.2.0/24): Contains the private EC2 instances.
2. Internet Gateway (IGW)
- The Public Subnet is associated with an Internet Gateway (IGW) to allow external SSH access.
3. Security Groups Configuration
- Bastion Host Security Group
- Allows SSH (port 22) access only from trusted IP addresses (e.g., administrator’s IP).
- Private EC2 Security Group
- Allows SSH (port 22) access only from the Bastion Host.
4. Route Tables
- The Public Subnet routes traffic to the Internet Gateway.
- The Private Subnet only allows internal communication (no direct internet access).
VPC:
A Virtual Private Cloud (VPC) is a private cloud in a public cloud that enables users to customize and control their network design, such as IP address range, subnets, route tables, and network gateways. VPCs enable an isolated space for securely running applications, supporting customization of network settings like security and access control. It's a fundamental service in cloud infrastructures like AWS, providing flexibility, scalability, and improved security for cloud resources.
IGW :
An Internet Gateway (IGW) is a component that connects a Virtual Private Cloud (VPC) to the internet in cloud environments like AWS. It enables instances within the VPC to communicate with the internet and vice versa. The Internet Gateway is essential for resources that require inbound and outbound internet access, such as web servers, email servers, or any public-facing applications.
Key functions of an Internet Gateway:
- Outbound traffic: Allows instances in the VPC to send requests to the internet (e.g., accessing external services or updating software).
- Inbound traffic: Permits external entities to access public-facing resources within the VPC (e.g., websites or APIs).
- High Availability: The Internet Gateway is designed to be highly available and automatically scales to handle traffic as needed.
Private Route Table:
A private route table in a cloud environment, like AWS, is a routing table that defines how network traffic is directed within a Virtual Private Cloud (VPC) for private subnets. Unlike public route tables, which route traffic to an Internet gateway, private route tables ensure that instances within private subnets do not have direct access to the internet.
Key Characteristics:
- Private Subnets: Private route tables are typically associated with private subnets, which are isolated from direct internet access. This helps secure sensitive resources, such as databases or application servers, that should not be exposed to the public internet.
- No Internet Gateway Route: Private route tables do not include routes that send traffic to the Internet Gateway. Instead, they may route traffic to a NAT gateway or NAT instance in a public subnet, which allows outbound internet access for private instances while preventing inbound internet access.
- Traffic Routing: Private route tables can route traffic between private subnets, allowing communication within the VPC. If an instance needs to access the internet (for example, to download updates), it can do so through a NAT device.
- Security and Control: By using a private route table, you can ensure that only specific traffic (such as through a VPN, Direct Connect, or NAT) reaches the internet, providing better security and network control.
Route Table :
A Route Table is a set of rules, or routes, used to determine how network traffic is directed within a Virtual Private Cloud (VPC) or subnet in cloud environments like AWS. Each route specifies the destination IP address (or range) and the target (next hop) that traffic should be forwarded to in order to reach that destination.
A Security Group
A Security Group in AWS is a virtual firewall that controls the inbound and outbound traffic to and from your AWS resources (such as EC2 instances, RDS instances, etc.). It acts as a rule-based access control mechanism to protect your instances by specifying which traffic is allowed or denied. Security Groups are associated with EC2 instances and other AWS services that require network access.
A Public Security Group :
A Public Security Group is used for resources that need to be accessed from the internet, such as web servers or load balancers. It allows inbound traffic from external sources while controlling which types of connections are permitted, such as HTTP or HTTPS.
A Private Security Group :
A Private Security Group is designed for resources that should not be exposed to the internet, like application servers or databases. It restricts inbound traffic, allowing access only from trusted sources within the same private network or Virtual Private Cloud (VPC). These groups help secure internal resources while enabling controlled communication between different instances.
Public Subnet:
A Public Subnet is a subnet within a Virtual Private Cloud (VPC) where resources, such as EC2 instances, are directly accessible from the internet. This is typically used for resources that need to be publicly reachable, such as web servers or load balancers.
Private Subnet:
A Private Subnet is a subnet within a VPC where resources are not directly accessible from the internet. This subnet is typically used for internal resources that should be isolated from the internet for security reasons.
Public IP:
A Public IP (also known as a Public IP Address) is an IP address that is routable over the internet. These addresses are globally unique and assigned to devices that need to be accessed over the internet. Public IPs are typically used for resources that need to be reachable from outside a private network, such as web servers, mail servers, and load balancers.
Private IP:
A Private IP (also known as a Private IP Address) is an IP address used within a private network that is not routable over the internet. These addresses are used for devices that do not need to be directly accessible from outside the network, such as internal servers, databases, or application instances.
Public Instance:
- Accessible from the Internet: Public instances have a public IP address and can be accessed directly from the internet.
- Use Case: These are often used for web servers, load balancers, or any service that needs to be accessed by users or other services outside the VPC (Virtual Private Cloud).
- Security Considerations: While public instances are accessible, they should still have proper security groups and firewalls in place to control inbound/outbound traffic and prevent unauthorized access.
Private Instance:
- Not Accessible from the Internet: Private instances are isolated from the internet and can only communicate with other instances within the VPC or through VPN/Direct Connect setups.
- Use Case: Typically used for databases, application servers, or backend services that do not need direct exposure to the public internet.
- Security Considerations: Private instances are more secure in that they are hidden from the public, reducing the attack surface. Communication can be controlled through VPC routing and security groups.
Conclusion
A Bastion Host is a vital security component in AWS, enabling secure access to private EC2 instances while minimizing exposure to potential attacks. By implementing best practices such as restricted access, key-based authentication, and logging, organizations can enhance the security of their cloud infrastructure. Alternatively, AWS Systems Manager Session Manager offers a more secure and managed approach, eliminating the need for traditional SSH-based access.