Understanding Public and Private Subnets in AWS
Introduction
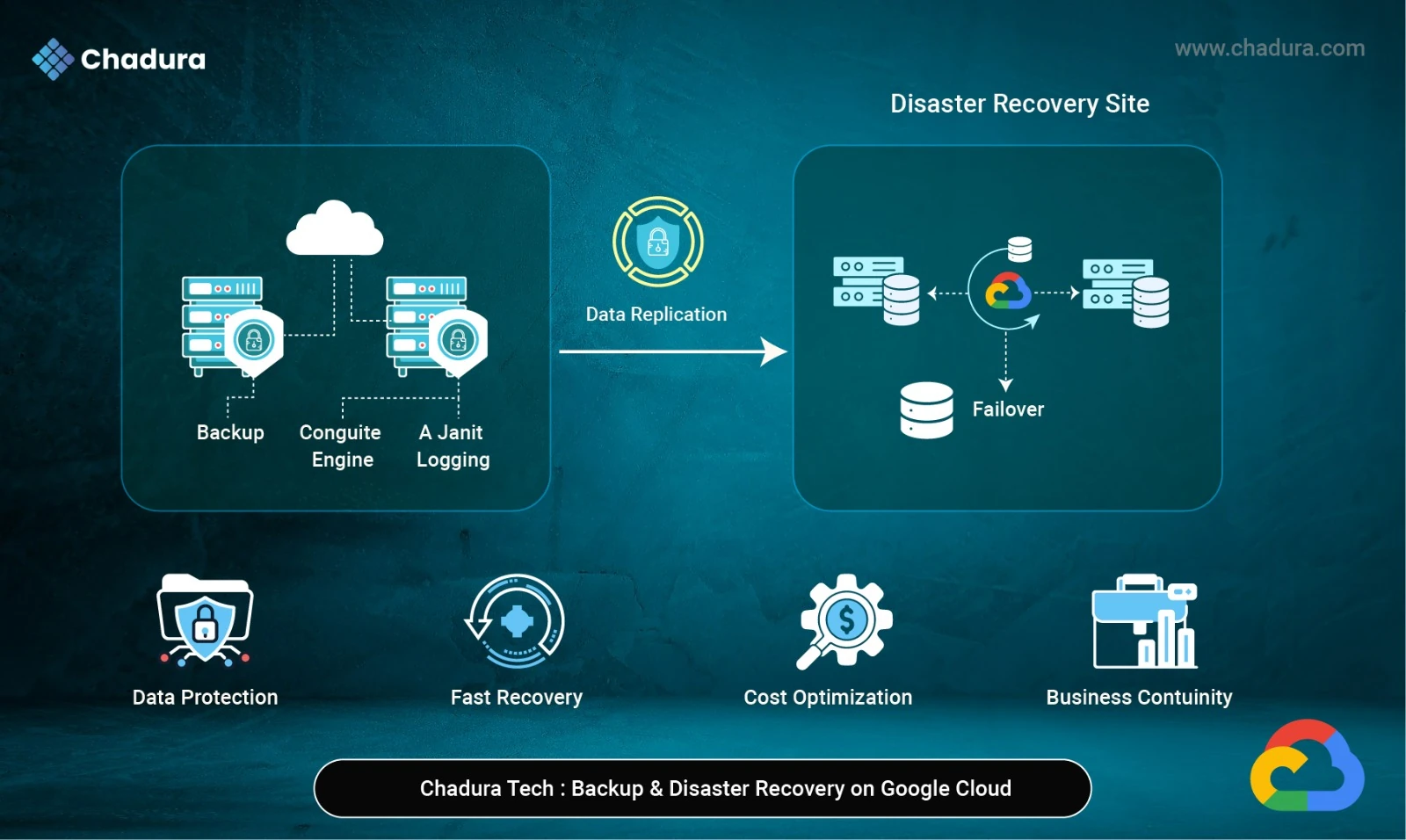
In AWS Virtual Private Cloud (VPC), subnets play a crucial role in segmenting and Organizing resources within a network. AWS subnets are categorized into public subnets and private subnets, based on their accessibility to the internet. Understanding their differences and use cases is essential for designing a secure and efficient cloud infrastructure.
What is a Public Subnet?
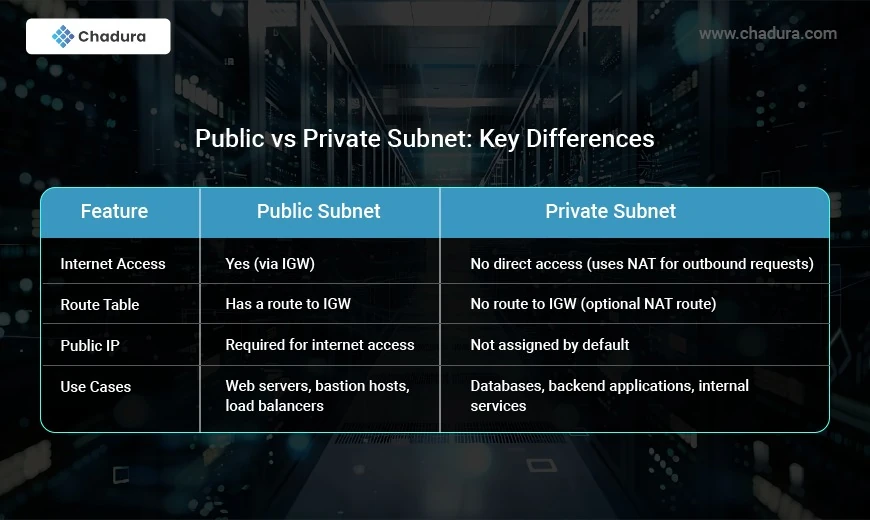
A public subnet is a subnet within a VPC that has direct access to the internet. It is typically used for resources that need to be publicly accessible, such as web servers, bastion hosts, and load balancers.
Key Characteristics of Public Subnets:
Internet Gateway (IGW): Public subnets are associated with an Internet Gateway, which enables instances within them to send and receive traffic from the internet.
Public IP or Elastic IP: Instances in a public subnet must have a public IP or Elastic IP (EIP) to communicate over the internet.
Route Table Configuration: The subnet’s route table must have a route to the Internet Gateway, allowing external connectivity.
Use Cases for Public Subnets:
- Hosting web applications and APIs.
- Load balancers for distributing traffic.
- Bastion hosts for secure SSH/RDP access to private instances.
What is a Private Subnet?
A private subnet is a subnet that has no direct access to the internet. It is used for hosting internal resources that should remain isolated from external traffic, such as databases, application servers, and backend services.
Key Characteristics of Private Subnets:
No Direct Internet Access: Private subnets do not have routes to an Internet Gateway.
NAT Gateway or NAT Instance (Optional): To allow outbound internet access (e.g., for updates or external API calls), instances in a private subnet can use a NAT Gateway or a NAT Instance.
Route Table Configuration: Private subnets do not have a direct route to the Internet Gateway but may have routes to a NAT Gateway in a public subnet for outbound traffic.
Use Cases for Private SubNets:
- Hosting databases (e.g., RDS, NoSQL databases).
- Application servers and microservices.
- Backend processing systems.
- Internal services that do not require internet exposure.
Public Vs Private Subnet
Conclusion
Public and private subnets in AWS play a vital role in designing secure and scalable cloud architectures. Public subnets host externally accessible resources, while private subnets keep sensitive data and backend systems isolated. By implementing a well-structured subnet strategy, organizations can enhance security, optimize performance, and ensure efficient cloud resource management.
AWS Route Tables: A Guide to Network Traffic Control
Introduction
AWS Route Tables are an essential component of Amazon Virtual Private Cloud (VPC), responsible for directing network traffic within a cloud infrastructure. Properly configured route tables ensure seamless communication between different subnets, external networks, and internet-facing resources.
What is an AWS Route Table?
An AWS Route Table is a set of rules (routes) that define how network traffic is directed within a VPC. Each VPC automatically comes with a main route table, which controls routing for all subnets unless explicitly associated with a different custom route table.
Key Components of a Route Table
A route table consists of:
- Routes: Define where the network traffic should be sent based on the destination IP range.
- Destination: Specifies the IP range to which the rule applies.
- Target: Defines the next hop for traffic (e.g., local, Internet Gateway, NAT Gateway, VPC Peering, etc.).
- Subnet Associations: Determines which subnets use a particular route table.
Types of Route Tables
Main Route Table: The default route table that automatically applies to all subnets in a VPC unless overridden.
Custom Route Tables: User-defined route tables that can be explicitly associated with specific subnets.
Edge Association Route Table: Used in AWS Transit Gateway setups to manage cross-VPC communication.
Common Routing Scenarios
1. Public Subnet Route Table (For Internet-Facing Resources)
This configuration allows instances in the subnet to communicate with the internet via the Internet Gateway.
2. Private Subnet Route Table (For Internal Communication)
Here, internet-bound traffic from the private subnet is routed through a NAT Gateway, ensuring outbound access while preventing inbound connections.
3. VPC Peering Route Table (For Inter-VPC Communication)
This enables communication between different VPCs using a VPC Peering connection.
AWS Internet Gateway: Enabling Internet Access in Your VPC
Introduction
An AWS Internet Gateway (IGW) is a crucial component for enabling communication between resources in an Amazon Virtual Private Cloud (VPC) and the public internet. It serves as a gateway to facilitate inbound and outbound traffic for instances that require internet connectivity. This article explores how an Internet Gateway works, its use cases, and best practices for secure deployment.
What is an AWS Internet Gateway?
An Internet Gateway is a highly available, scalable, and redundant AWS-managed service that provides internet access to instances within a VPC. It operates horizontally and does not introduce network bottlenecks, ensuring seamless communication between AWS resources and the internet.
Key Features of an Internet Gateway
- Two-Way Traffic Handling: Supports both inbound and outbound connections.
- Scalability: AWS automatically scales IGW to handle traffic loads.
- High Availability: IGW is a fully managed service with built-in redundancy.
- No Cost: AWS does not charge for Internet Gateway usage.
How an Internet Gateway Works
An IGW is attached to a VPC and works alongside route tables, security groups, and network ACLs to manage traffic flow. It does not perform network address translation (NAT) but allows instances with a public IP or Elastic IP (EIP) to send and receive traffic from the internet.
Diffrence between NAT Gateway Internet Gateway