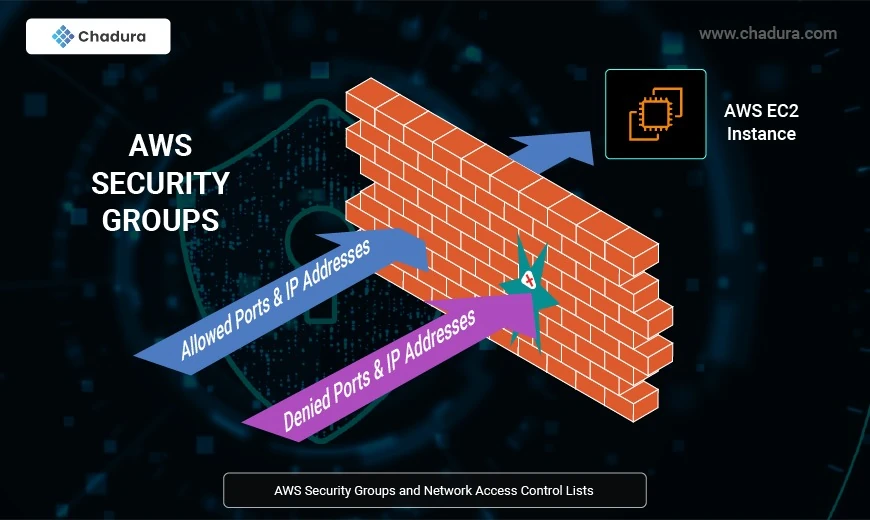
Real-World Use Cases for AWS Security Groups and Network ACLs (NACL)
Before delving into best practices, it’s essential to understand what AWS Security Groups are. They act as virtual firewalls for your EC2 instances to control both inbound and outbound traffic. Unlike Network Access Control Lists (NACLs), Security Groups are stateful; if you send a request from your instance, the response traffic for that request is allowed to flow in regardless of inbound security group rules.
1. Principle of Least Privilege
Restrictive Rules: Configure Security Group rules to be as restrictive as possible. Only allow traffic necessary for your application to function. For instance, if your web server only needs to communicate on port 80 (HTTP) and 443 (HTTPS), do not open other ports.
2. Regular Audits and Reviews
Audit Rules: Regularly review and audit your Security Groups. Ensure that the rules are still relevant and necessary for your current architecture.
3. Avoid Using Default Security Groups
Custom Security Groups: Default Security Groups typically have broader permissions. Create custom Security Groups with specific rules that suit your application needs.
4. Use Descriptive Names and Tags
Naming Convention: Use clear, descriptive names and tags for your Security Groups. This practice helps in identifying their purpose and the resources they protect, making management easier.
5. Segregation and Micro-segmentation
Differentiate Security Groups: Use different Security Groups for different types of instances based on their roles (e.g., web servers, database servers). This segregation helps in applying the principle of least privilege effectively.
6. Integration with AWS Identity and Access Management (IAM)
IAM Policies: Integrate Security Groups with IAM to control who can create, modify, or delete Security Groups. This integration enhances security and governance.
7. Log and Monitor Security Group Changes
CloudTrail Integration: Use AWS CloudTrail for logging and monitoring changes to Security Groups. This approach helps in auditing and detecting unusual activities.
8. Avoid Opening Inbound Traffic from 0.0.0.0/0
Limit Exposure: Except for specific cases like a web server, avoid opening inbound rules to all IP addresses (0.0.0.0/0). This practice reduces the risk of attacks.
9. Regularly Update and Remove Unused Security Groups
Maintenance: Regularly update the rules as per changing requirements and delete unused Security Groups to keep your environment clean and manageable.
10. Use Security Group References
Referencing Security Groups: Instead of using IP ranges, reference other Security Groups when creating rules. This method is particularly useful in dynamic environments where IP addresses change frequently.
Key Features and Functions
- Stateful Filtering: Security Groups are stateful, meaning if an inbound rule allows traffic, the return traffic is automatically permitted, simplifying rule configurations.
- Security Group Rules: Rules can be configured based on IP protocols, port ranges, and source/destination IP addresses.
- Application-Level Security: They can be used to define rules that allow specific applications or services to communicate with the instances they’re associated with.
Configurations and Best Practices
- Least Privilege Principle: Security Groups follow the principle of least privilege, meaning only necessary ports and protocols should be opened.
- Ephemeral Ports: Ensure outbound rules allow traffic for ephemeral ports if applications require responses from external servers.
- Regular Review: Periodically review and audit security group configurations to ensure they align with security requirements and minimize any unnecessary exposure.
Use Cases
- Web Applications: Security Groups can be used to control traffic to web servers, allowing HTTP (port 80) and HTTPS (port 443) traffic.
Database Access Control: Restrict access to databases like MySQL (port 3306) or PostgreSQL (port 5432) to specific IP ranges.
Diffrence between SG and NACL - click here to create NACL steps
| S.No | Security Groups (SG) | Network Access Control List |
1 | Operates on Instance Level | Operates on Subnet Level |
2 | Stefull | Stateless |
3 | Denies all Traffic by default | Allow all Traffic by Default |
4 | Rules are combined together and Applied | Rules are applied in Ascending order until matched |
5 | Can add only one type of rule - allowed | Can add two type of rule - allowed/deny |
6 | Must be explicity attached to an instance | Automatically attached to all instance in a subnet |
7 | Works on top of NACL | First touch point for the traffic in subnet |
Network Access Control Lists (NACLs)?
AWS NACLs are stateless network-level security measures that control traffic in and out of subnets. Unlike Security Groups, which are instance-specific, NACLs operate at the subnet level.
Key Features and Functions
- Ordered Rule Evaluation: NACLs follow numbered rules in sequential order from lowest to highest, processing rules based on their order.
- Stateless Filtering: Unlike Security Groups, NACLs require explicit rules for both inbound and outbound traffic. If an inbound rule permits traffic, an outbound rule permitting the response traffic is required.
- Allow/Deny Rules: NACLs allow defining rules to explicitly allow or deny traffic based on IP addresses, protocols, and port ranges.
Configurations and Best Practices
- Careful Rule Configurations: Due to their stateless nature, ensure proper ingress and egress rules to allow necessary traffic while maintaining security.
- Regular Auditing: Similar to Security Groups, perform periodic audits to ensure NACLs align with security policies and minimize unnecessary exposure.
Use Cases
- Segmenting Workloads: NACLs can be used to segment workloads within a VPC, applying different levels of access control to different subnets.
- Additional Layer of Security: They provide an extra layer of security by filtering traffic at the subnet level, complementing the security provided by Security Groups.
Steps to Create a Security Group
Step1: Access the EC2 Dashboard
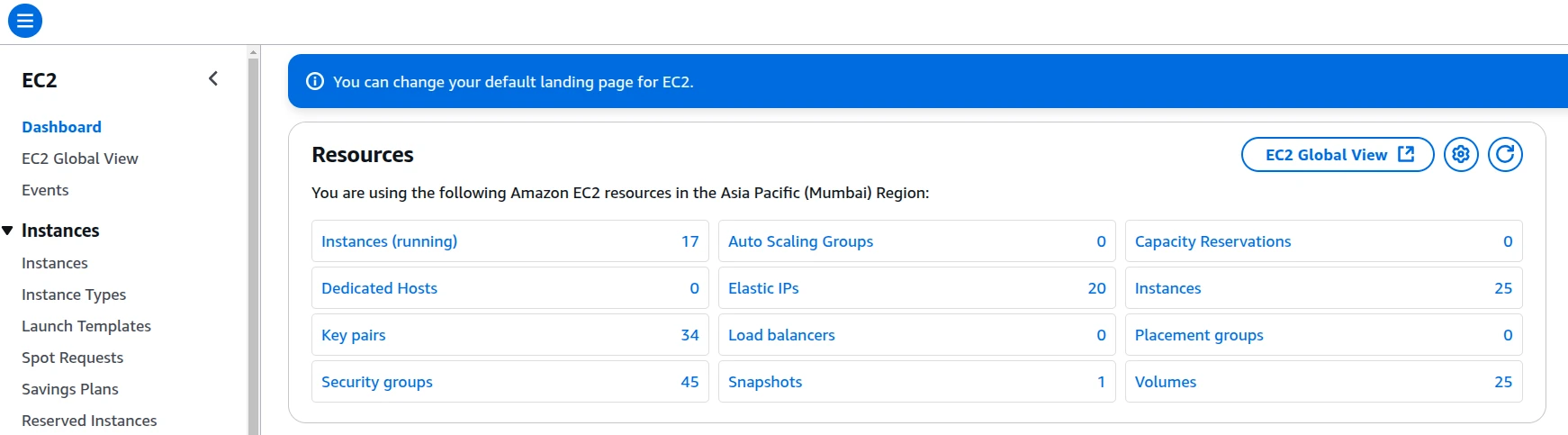
Step 2: Navigate to Security Groups
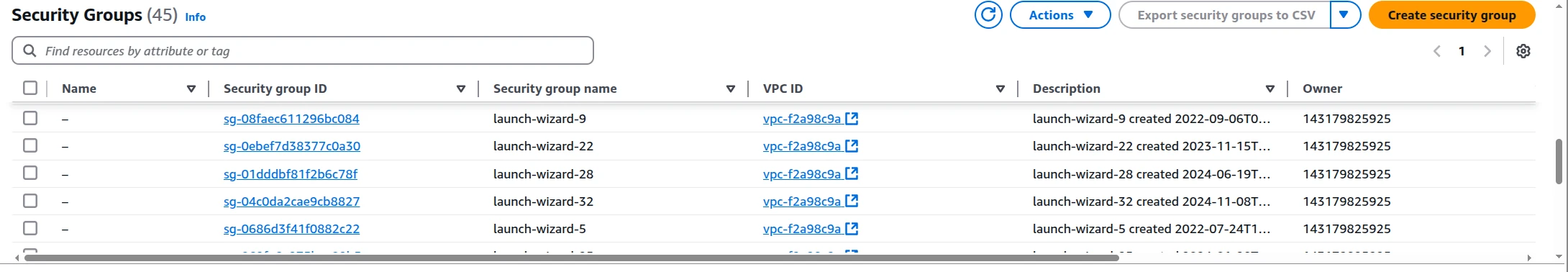
Step 3: Initiate Security Group Creation
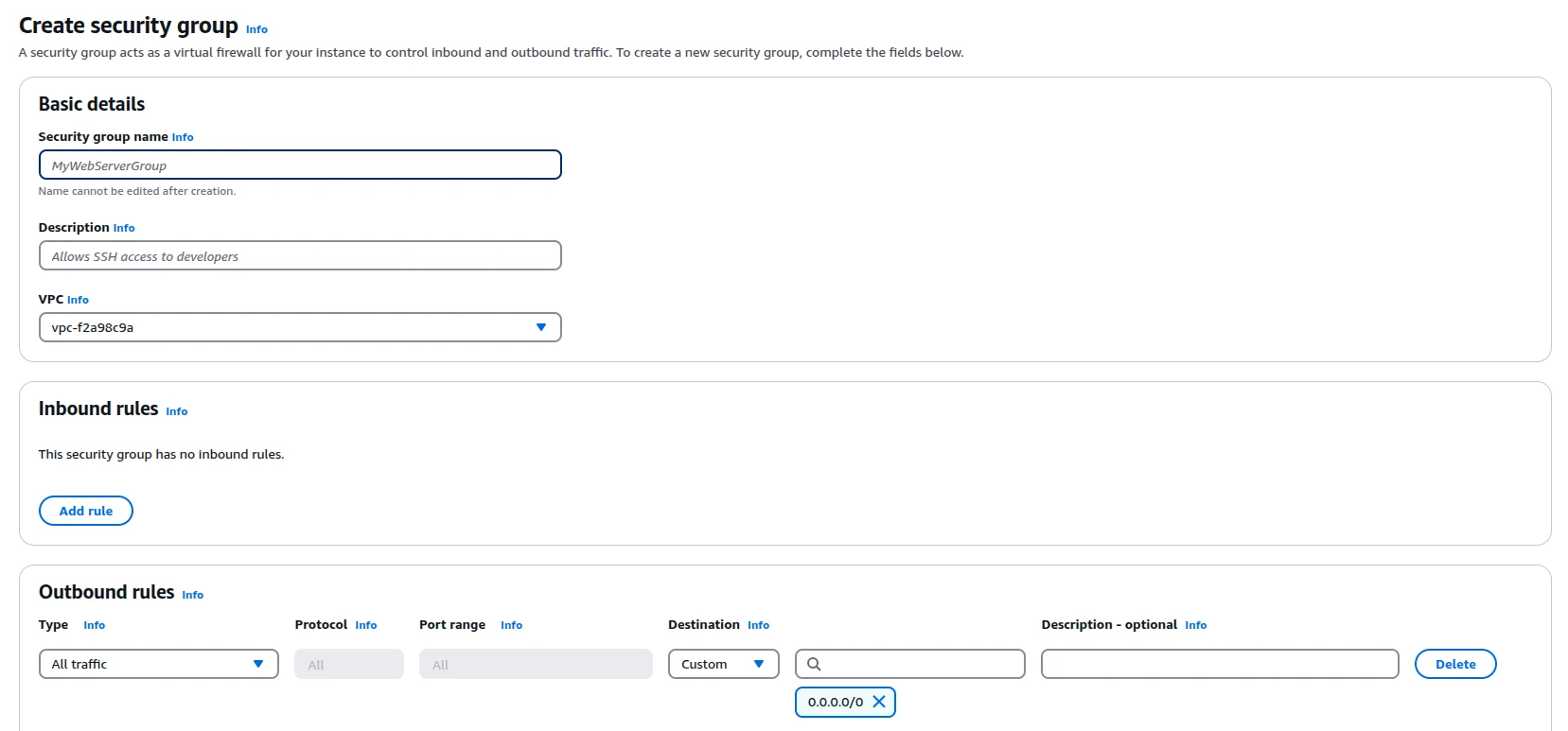
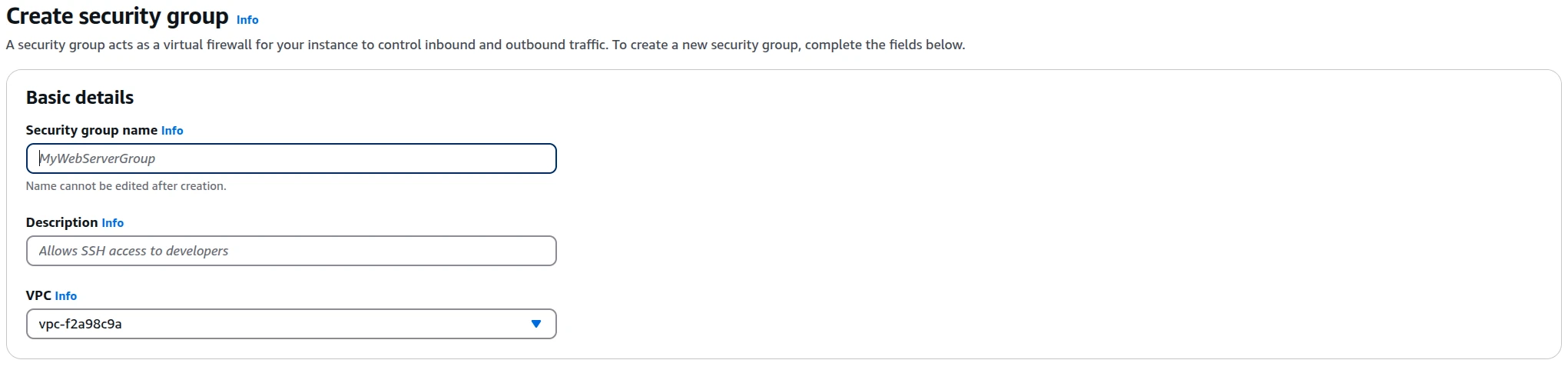
Step 4: Define Security Group Details
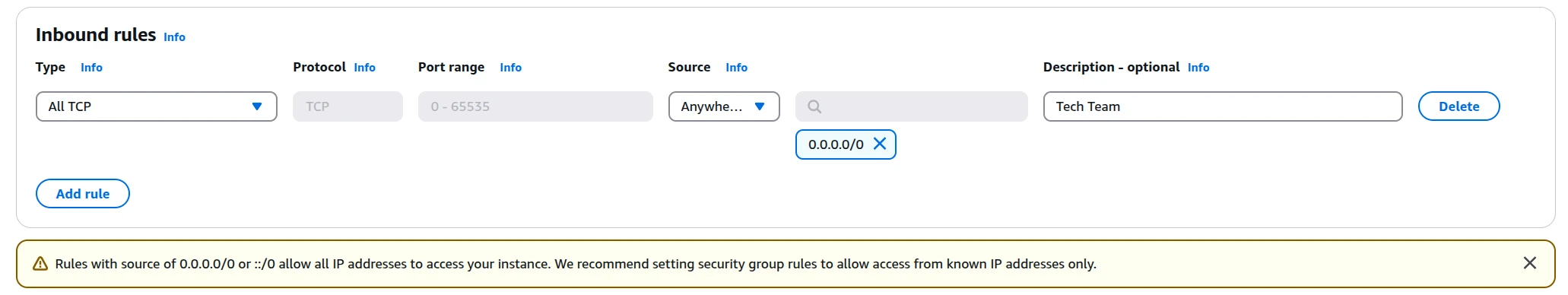
Step 5: Configure Inbound Rules
Step 6: Configure Outbound Rules
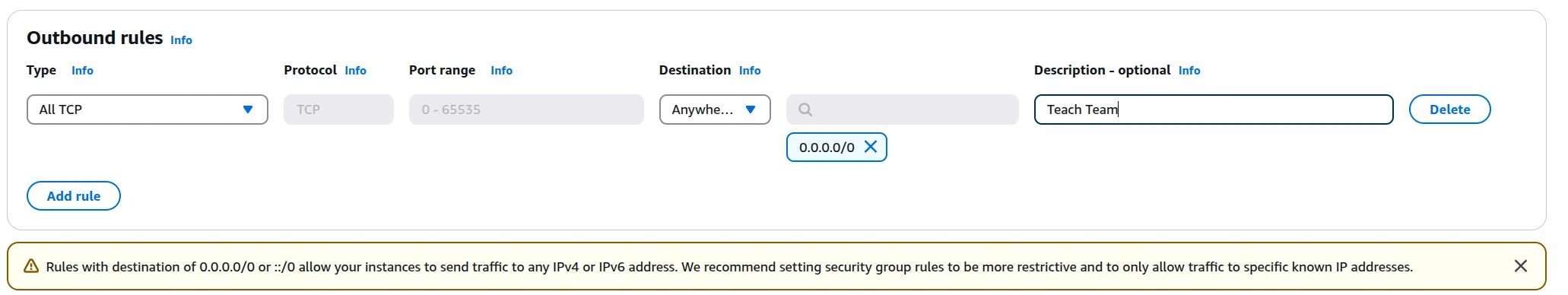
Step 7: Review and Create
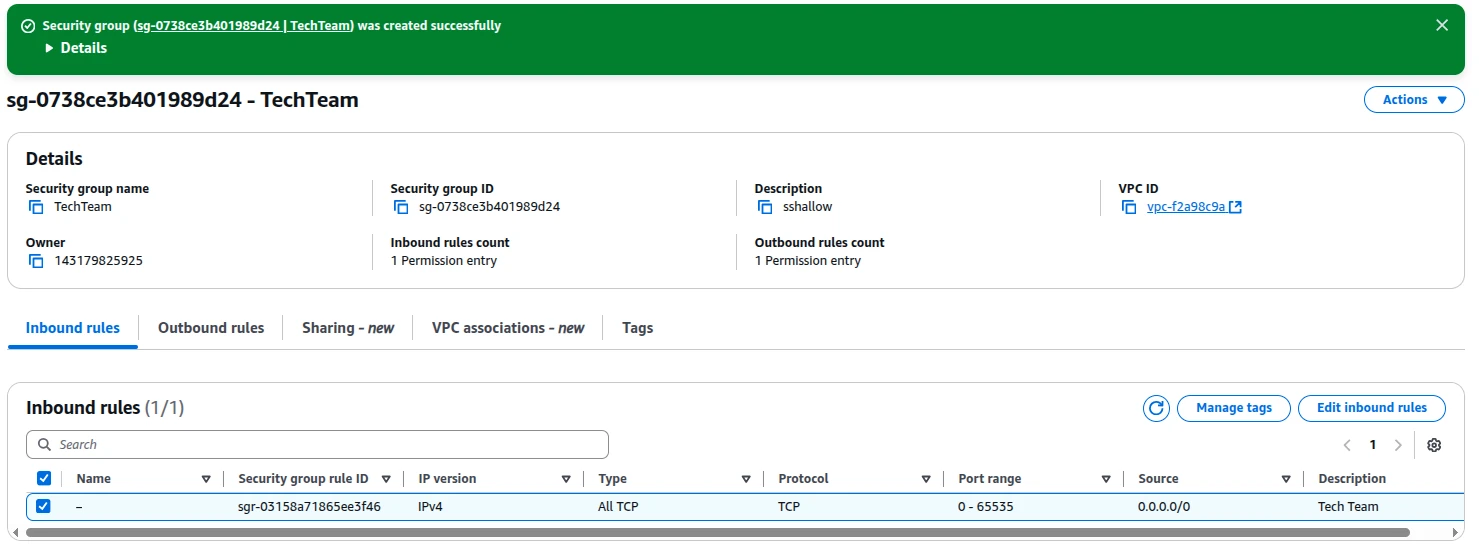
Conclusion
In the AWS environment, Security Groups and NACLs are critical to managing and securing network traffic. Security Groups work at the instance level with stateful filtering, whereas NACLs work at the subnet level with stateless filtering. Both are critical elements for the implementation of a strong security posture in AWS environments.